Creating a Generic OAuth2/OIDC IdP in Pangolin
In Pangolin, go to “Identity Providers” and click “Add Indentity Provider”. Select the OAuth2/OIDC provider option.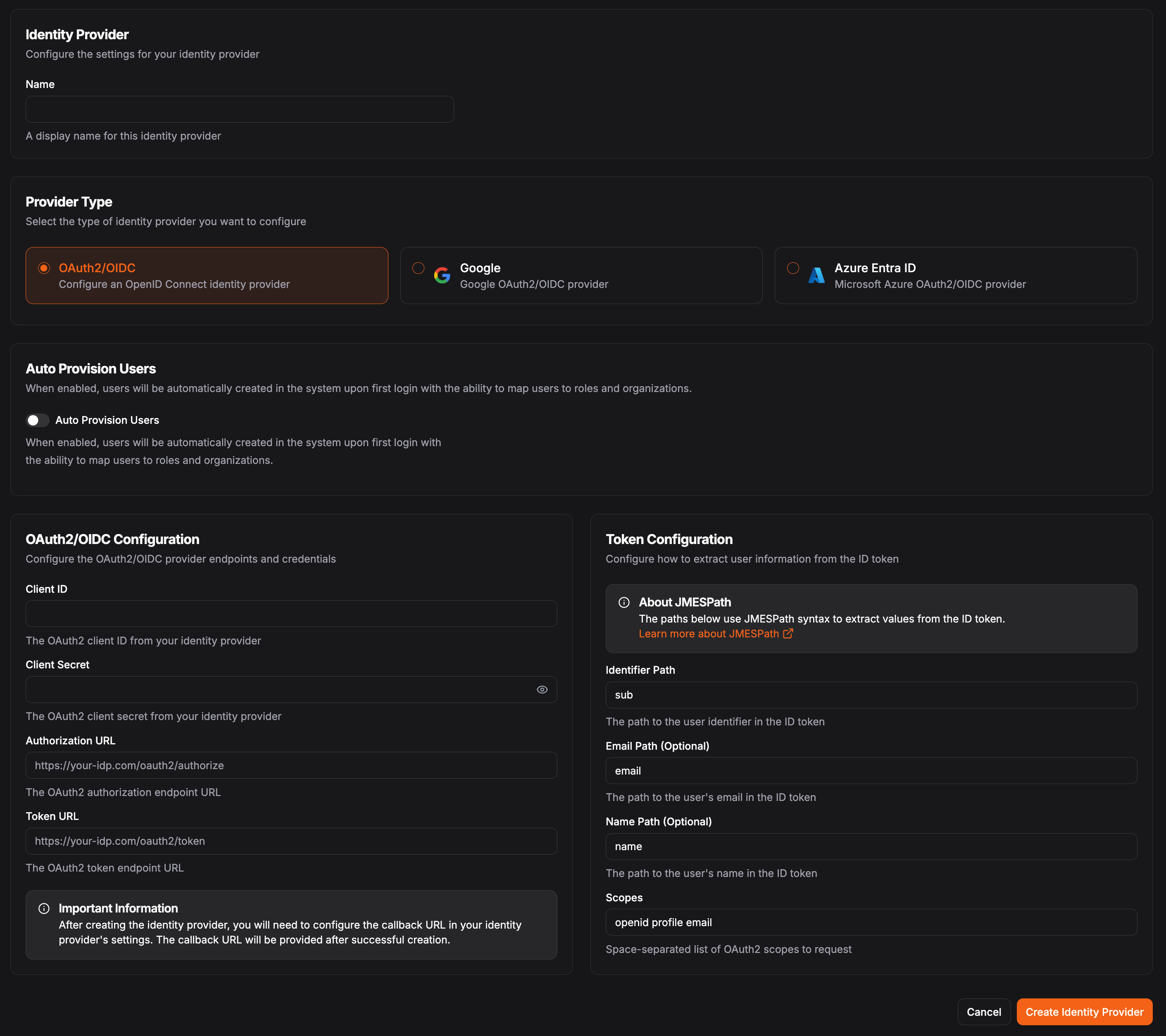
The client identifier provided by your identity provider.
The client secret provided by your identity provider.
The authorization endpoint URL from your identity provider.
The token endpoint URL from your identity provider.
Token Configuration
Use JMESPath to select attributes from the claims token. See JMESPath for more information on how to use JMESPath. Determine how to access information from the claims token returned by the identity provider. This is used to map the user information from the identity provider to the user information in Pangolin.This must be unique for each user within an identity provider.Example:
sub or user_idPath to the user’s email address in the claims token.Example:
emailPath to the user’s display name in the claims token.Example:
name or preferred_usernameThe scopes to request from the identity provider (not JMESPath; must be space-delimited strings).Default:
openid profile emailGenerally,
openid profile email is sufficient for most use cases.
