Enable Auto Provision
Toggle the “Auth Provision Users” switch when creating or editing an identity provider.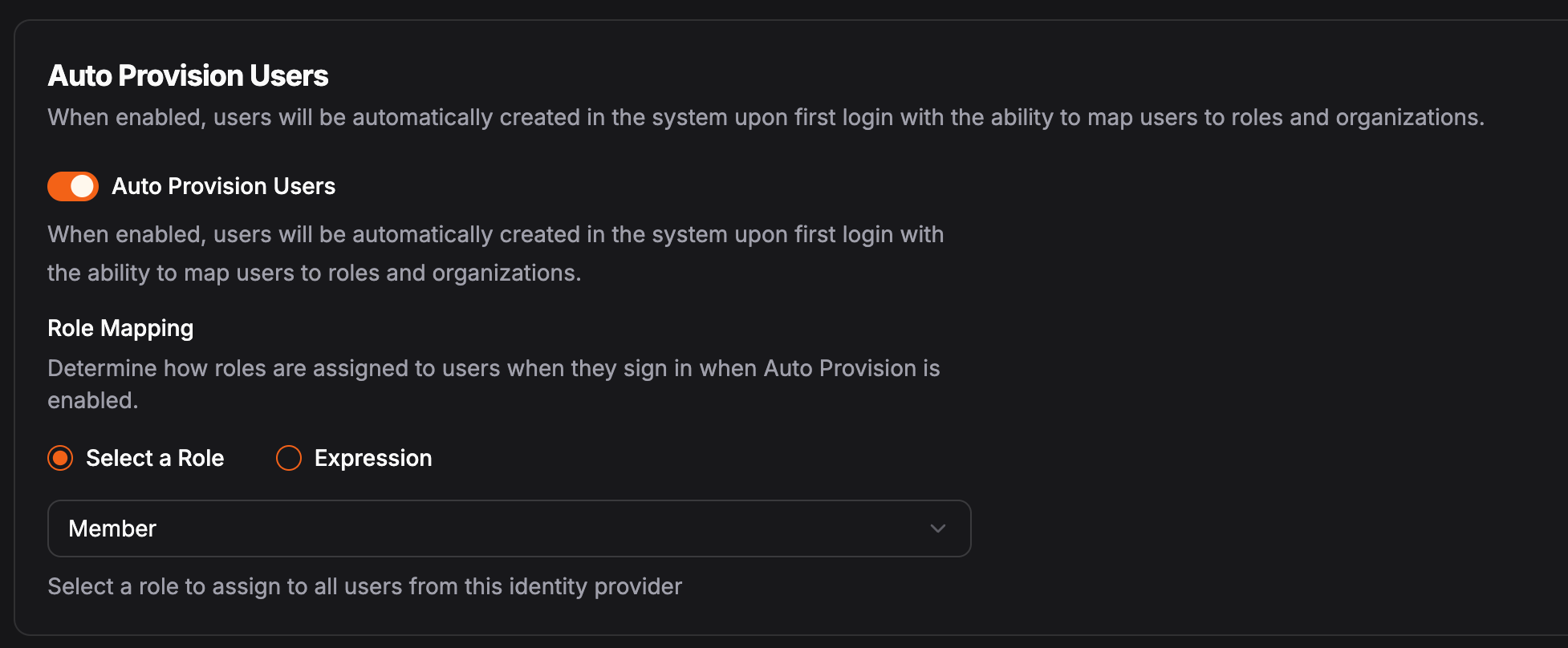
What if Auto Provisioning is Disabled?
If auto provision is disabled, organization admins will need to manually create the user accounts and select the role for each user. When creating a user, you can select the identity provider that the user will be associated with. A user will not be able to log in using the identity provider if a user is not pre-provisioned in the system.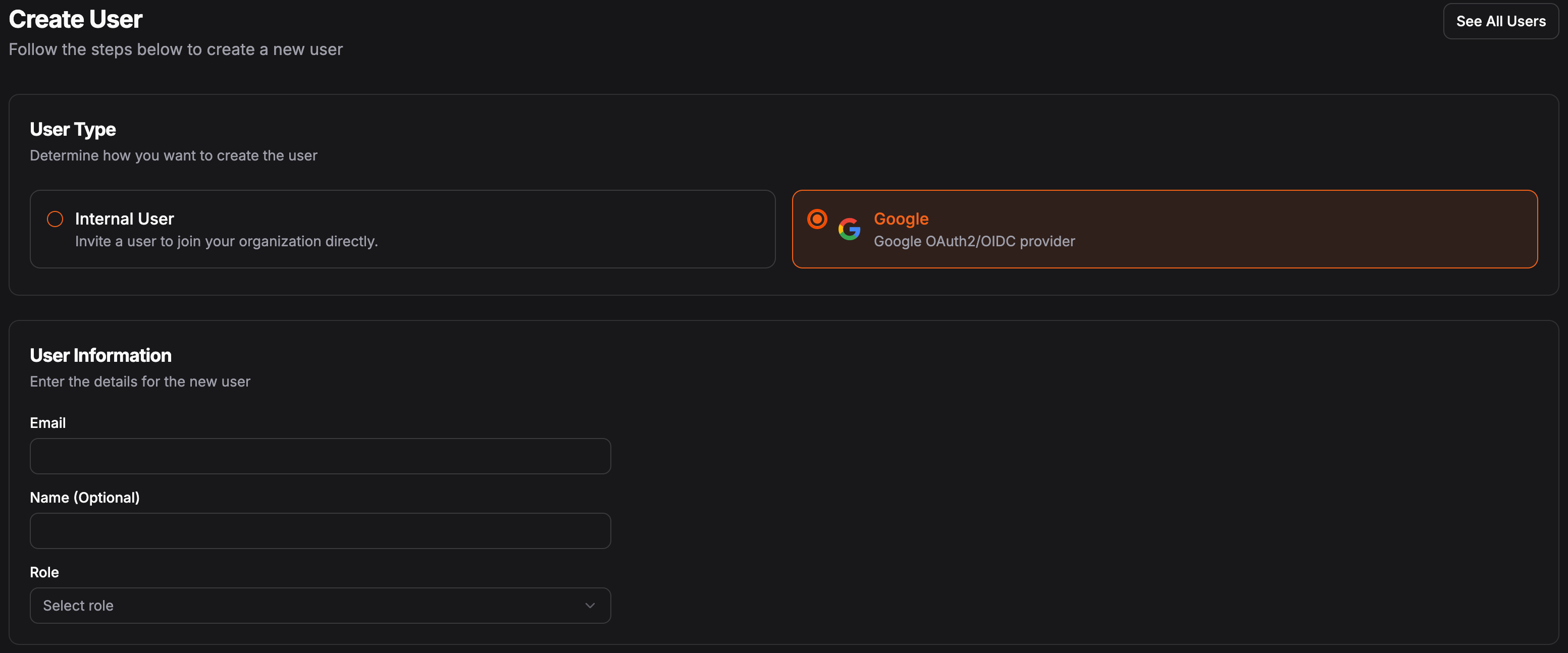
Configuration Options
Selecting Roles
You can choose between “Select a Role” and “Expression”. Selecting a role will apply that role to all auto provisioned users. The expression will be evaluated against the token response from the IdP on each login (see examples below). You can always manually change the role of the user after they’re provisioned.Expressions
Use JMESPath to map attributes from the identity provider to roles in Pangolin. See JMESPath for more information on how to use JMESPath. The expression will be matched against each organization. Meaning:- The result of the expression must return the exact string of the role name as it is defined in the organization.
- If no matching role is found, the user will not be added to the organization.
Example: Role Selection
Expression:Community Edition
In the Community Edition, identity providers are managed at the server level and not the individual organization. This means you must define policies per organization to map users to specific organizations and roles within those organizations. After you create an IdP, on the edit page, you can manage organization policies via the “Organization Policies” tab. You can set default (fallback) policies, or define them on a per org basis.How Organization Policies Are Evalutated
It is helpful to think of the auto provisioning process as follows:1
User Login
User successfully logs in using an identity provider.
2
Account Creation
Pangolin creates a user account for the user.
3
Organization Evaluation
Pangolin will loop through each organization and evaluate the JMESPath expression for the organization. If the expression does not return true or the same ID as the current organization, the user will not be added to the organization.
4
Role Assignment
For each organization, Pangolin will evaluate the JMESPath expression for the role. If no role is found with the exact name in that organization, the user will not be added to the organization.
Selecting Organizations
Use JMESPath to map attributes from the identity provider to organizations in Pangolin. See JMESPath for more information on how to use JMESPath. The expression will be matched against each organization. Meaning:- The result of the expression must return true or the organization ID as it is defined in the system.
- If no matching organization is found, the user will not be added to the organization.
{{orgId}} in the expression. This will be replaced with the organization ID when the expression is evaluated.
Example 1: Group-based Selection
Expression:Example 2: Fixed Organization
Expression:Default (Fallback) Policy
You can optionally configure a default policy for all organizations. This will be used if the organization does not have its own policy configured. This example will always return ‘home-lab’ meaning the user will always be added to the “home-lab” organization.Example 1: Dynamic Organization Selection
Expression:{{orgId}} with “home-lab”. The result of the expression will return true since the user is a member of the “home-lab” group.
