Identity providers allow your users to log into Pangolin and Pangolin resources using their existing accounts from external identity systems like Google, Microsoft Azure, or Okta. Instead of creating separate Pangolin accounts, users can authenticate with their familiar work or personal credentials.
Here is an example using Microsoft Azure Entra ID as SSO for Pangolin:
This feature is for you if:
- Your organization already uses an identity provider like Google Workspace, Microsoft Entra ID, Okta, or similar systems
- You want to centralize user management and avoid maintaining separate Pangolin accounts
- You need to control who can access Pangolin resources through your existing user directory
- You want users to access Pangolin using their existing credentials without creating new passwords
Supported Identity Providers
OAuth2/OIDC
This can be used to connect to any external identity provider that supports the OpenID Connect protocol such as:
- Authentik
- Keycloak
- Okta
- Other OIDC-compliant providers
Google
Google IdP is only available in Pangolin Cloud and Managed Self-hosted.
Azure Entra ID
Azure Entra ID IdP is only available in Pangolin Cloud and Managed Self-hosted.
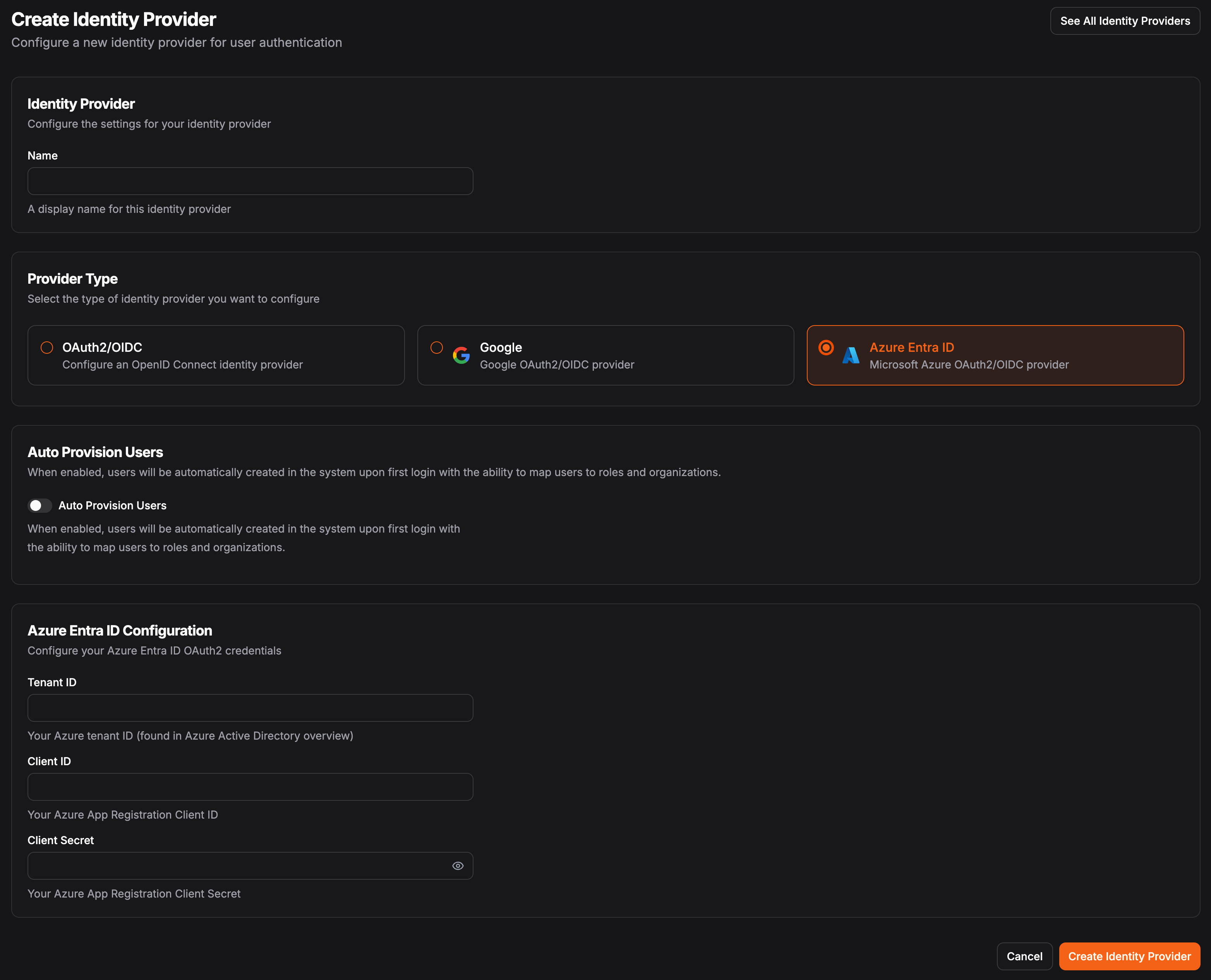
How to Add an Identity Provider
Navigate to Identity Providers
In the Pangolin organization, select the “Identity Providers” section in the sidebar.
Add New Provider
Click on the “Add Identity Provider” button.
Select Type
Select the type of identity provider you want to add (OAuth2/OIDC, Google, Azure Entra ID).
Set up Auto Provisioning (Optional)
Select the “Auto Provision Users” checkbox to automatically provision users and assign roles in Pangolin when they log in using an external identity provider. See Auto Provision for more information.If this is disabled, you will need to pre-provision a user in Pangolin before they can log in using an external identity provider. Configure Settings
Fill in the required fields for the selected identity provider type.
Custom Login Page
You can configure a custom login page for your organization to be served at a domain of your choice. The log in page for every resource will be served at this URL. Additionally, you can visit this url to log in to the organization itself to access the Pangolin dashboard. This is particularly useful for identity providers because it creates a place for your users to go to select the identity provider of choice to access the Pangolin dashboard.
Auto Provisioning
See Auto Provision for more information on how to automatically provision users and assign orgs and roles in Pangolin when they log in using an external identity provider.